Blocking Spammy Signups
We've been dealing with a fair amount of signups that are either triggered programmatically or by using fake email addresses. This is a bit of a hassle for us--not only are these signups taking advantage of the 50 free calls on our free tier (which actually costs us), it's also a pain for our sales team to sift through fake leads.
Identifying these signups programmatically was proving to be quite difficult though. The attackers were using a variety of proxy IPs and there weren't obvious similarities between requests. This is a write-up of our fixes so far, which should prove useful for companies in similar situations.
First attempt: captcha
The problem came to a head when we started getting a few automated signups every second--we needed a solution fast. Our first step was to add a captcha to the flow. Google's Recaptcha had just got a new facelift and seemed like a good option. Repaptcha tries to be intelligent and only prompt the user to fill in a captcha when they seem suspicious (lack of mouse movements, etc).
In theory this sounds great--nobody likes typing in captchas. In practice however, it seems the new version of Recaptcha is susceptible to brute forcing. We were still seeing the automated signups, but at a much lower rate (about one per minute).
Second attempt: blacklist domains
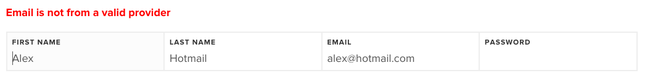
Some email providers are better than others at preventing people creating fake accounts. We noticed that all these dodgy signups were using hotmail.com as a provider. We also noticed that we'd never had a legitimate signup with an email using hotmail.com, let alone a paying customer. So we ultimately took the step of adding it to a blacklist. For good measure we also banned all anonymous email signups (like Mailinator).
Again, no success - our attackers just moved to gmail addresses. The game of cat and mouse continued.
Third time lucky
While we were pretty hesitant to add an email confirmation step, it seemed like a logical next step. I'm personally not a big fan of breaking a user's signup flow (making them leave to check their inbox and click on a confirmation link). But it seemed we didn't have a choice.
What we realized though, is that Clearbit has excellent data for determining the likelihood that an email address is fake. If our APIs can't find any social data on an email, or any company data related to an email's domain, then that's fairly suspicious. So whenever we get a signup we do a quick Clearbit lookup on the email--if it seems fake we ask them to confirm. Otherwise we pass them straight through.
So far this approach is working fairly well and has the added benefit of not decreasing conversion rates. However if our attackers get hold of a set of valid email addresses (and start programmatically clicking on email confirmation links) then we'll have to think again. Either adding a credit card auth step, phone number validation, Facebook connect, or perhaps removing the free tier entirely.